| images | ||
| bicep | ||
| ExportedTemplate-HoneyPot.zip | ||
| geoip-summarized.csv | ||
| map.json | ||
| README.md | ||
azure_soc
azure_soc
Azure Sentinel Honeypot with Geographic Attack Visualization
A cybersecurity project demonstrating the deployment of a Windows honeypot in Azure with real-time attack monitoring and geographic visualization using Azure Sentinel.
Project Overview
This project creates a vulnerable Windows virtual machine (honeypot) in Azure to attract malicious actors, then uses Azure Sentinel to collect, analyze, and visualize security events with geographic context. The setup monitors failed RDP login attempts and displays attack origins on an interactive world map.
Architecture
- Azure Subscription: Cloud platform hosting all resources
- Resource Group: Container for project resources
- Virtual Network: Isolated network environment
- Windows VM (Honeypot): Intentionally vulnerable target system
- Log Analytics Workspace: Centralized log collection and analysis
- Azure Sentinel: SIEM solution for threat detection and visualization
- Geographic Data Integration: IP-to-location mapping for attack visualization
Prerequisites
- Active Azure subscription
- Basic understanding of Azure services
- RDP client for VM access
- PowerShell/Azure CLI (optional)
Implementation Steps
1. Initial Azure Setup
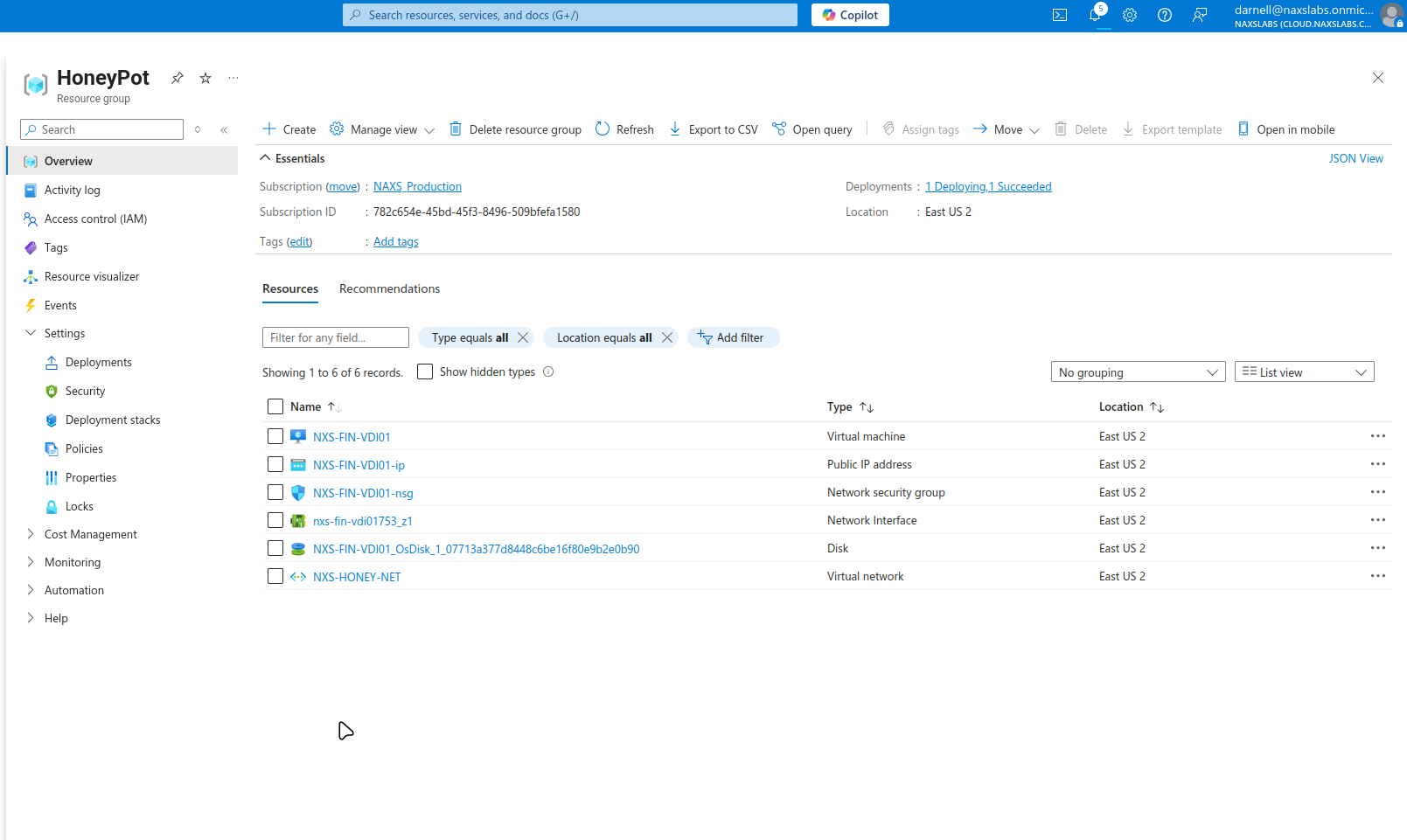
Create Resource Group
- Navigate to Azure Portal
- Create new Resource Group
- Select appropriate region
- Name the resource group (e.g.,
honeypot-rg)
Create Virtual Network
- Create Virtual Network in the same resource group
- Configure address space (e.g., 10.0.0.0/16)
- Create subnet for VM placement
- Use default DNS and security settings
2. Honeypot VM Deployment
VM Configuration
- Create new Windows Virtual Machine
- VM Details:
- Name:
honeypot-vm - Username:
naxslabs - Password:
Password123! - Size: Standard B2s (or similar)
- Name:
- Place in created resource group and virtual network
- Configure networking settings
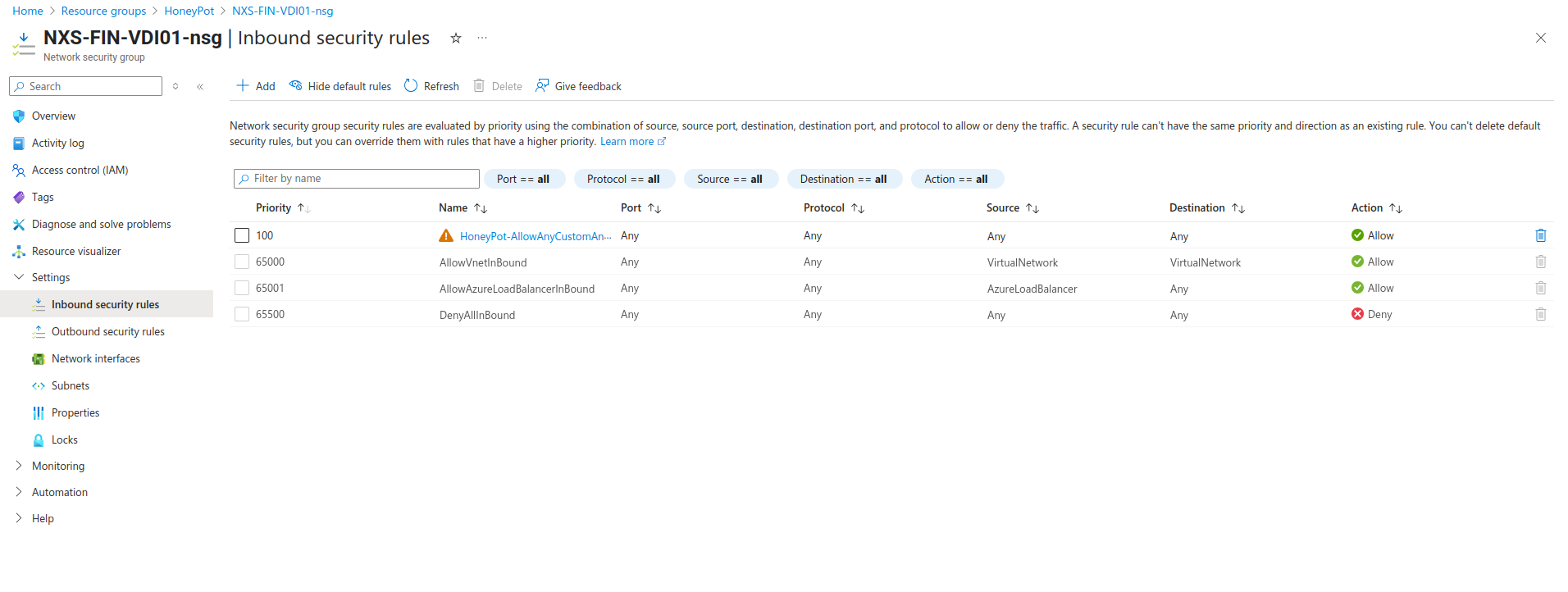
Security Configuration (Intentionally Permissive)
- Remove default RDP rule from Network Security Group
- Create new inbound rule:
- Source: Any (0.0.0.0/0)
- Destination: Any
- Protocol: Any
- Action: Allow
- Priority: 100
- Name:
HoneyPot-AllowAnyCustomAny
[Screenshot: NSG rule configuration]
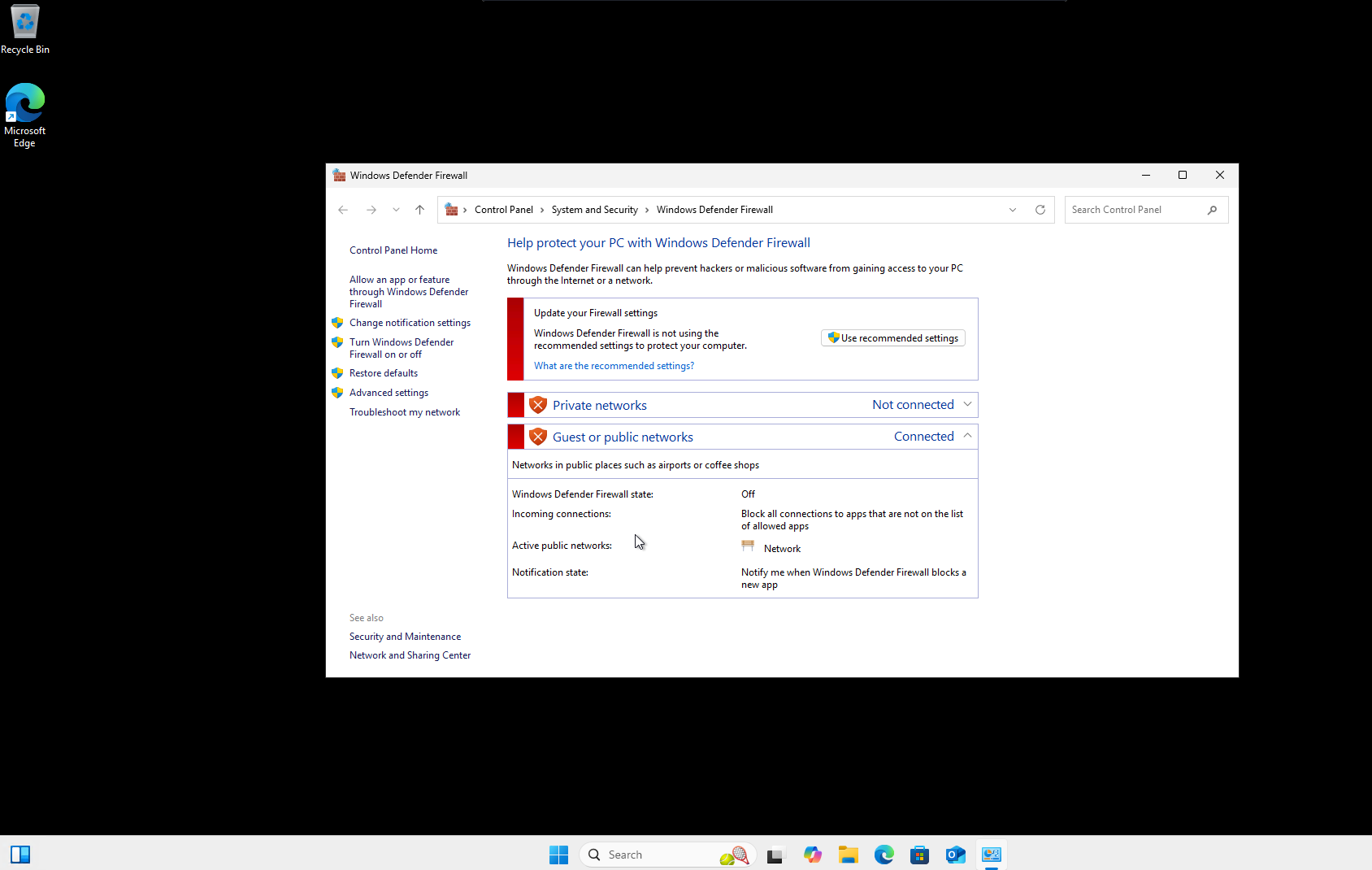
3. Disable Defender Firewall
Access VM via RDP
- Connect to VM using public IP
- Login with credentials:
naxslabs/Password123!
Disable Windows Firewall
- Open Windows Defender Firewall
- Turn off firewall for all network profiles:
- Domain network
- Private network
- Public network
4. Generate Test Security Events
Failed Login Attempts
- Attempt RDP connections with incorrect usernames
- Try various common usernames (admin, administrator, guest, etc.)
- Generate multiple failed login events
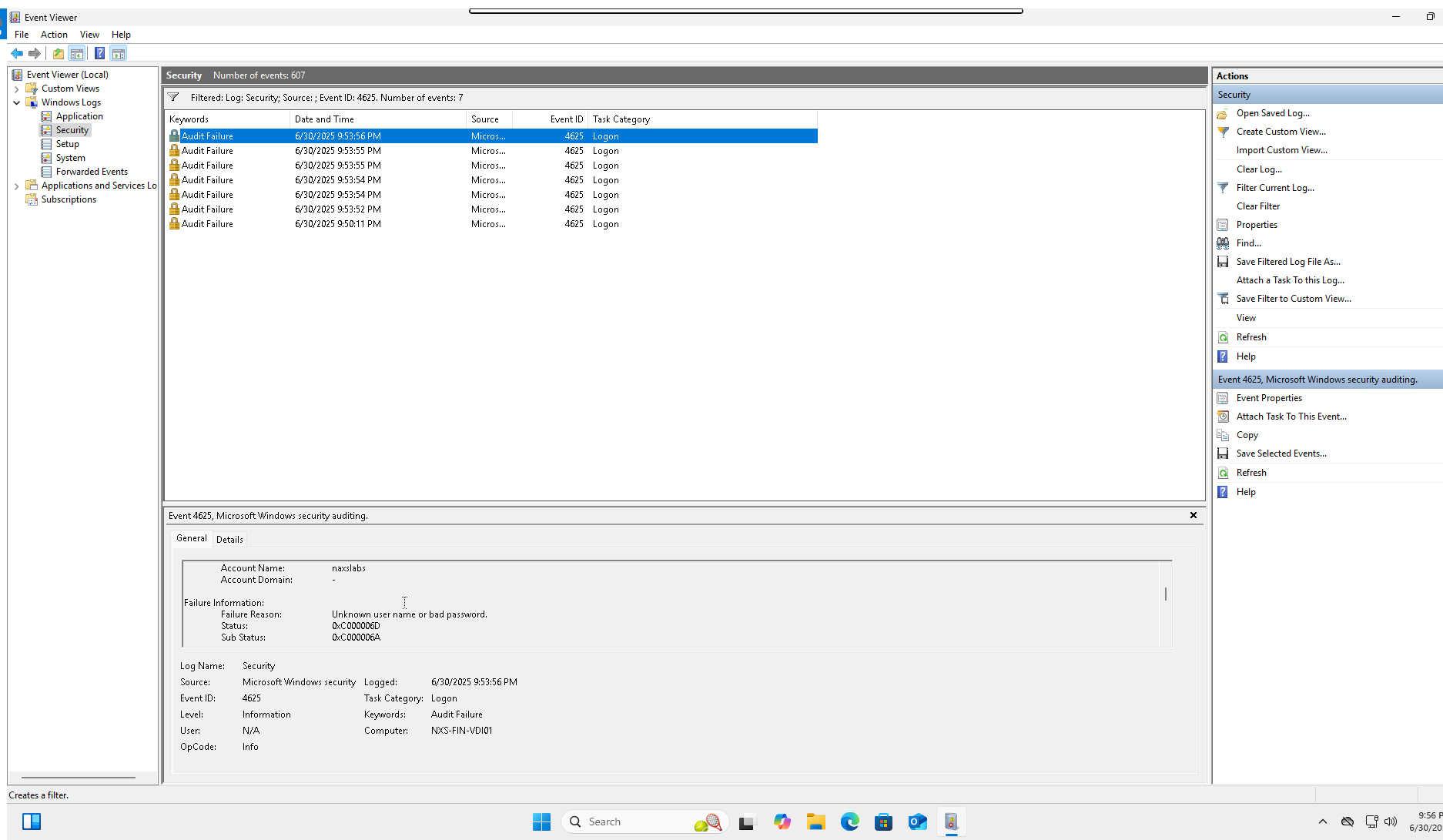
Verify Event Generation
- Open Event Viewer on honeypot VM
- Navigate to Windows Logs > Security
- Filter for Event ID 4625 (Failed logon attempts)
- Verify events are being generated with source IP addresses
5. Log Analytics Workspace Setup
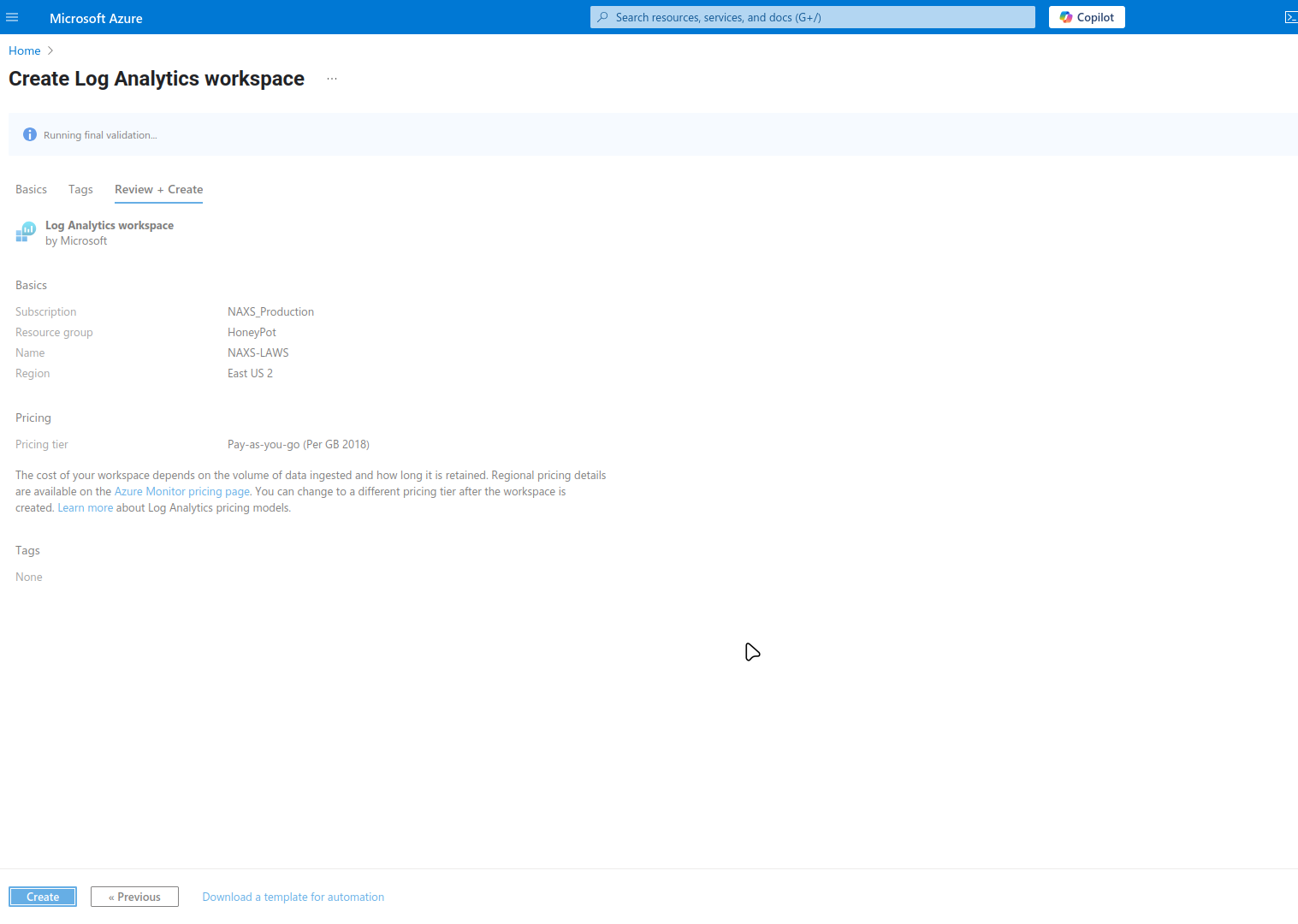
Create Log Analytics Workspace
- Create new Log Analytics Workspace
- Place in same resource group
- Select appropriate region and pricing tier
6. Azure Sentinel Configuration
Enable Sentinel
- Navigate to Azure Sentinel
- Connect Sentinel to the Log Analytics Workspace
- Wait for deployment to complete
Install Data Connectors
- Go to Sentinel > Content Hub
- Install Windows Security Events connector
- Install Azure Monitor Agent (AMA) connector
- Configure connectors to collect Security Events
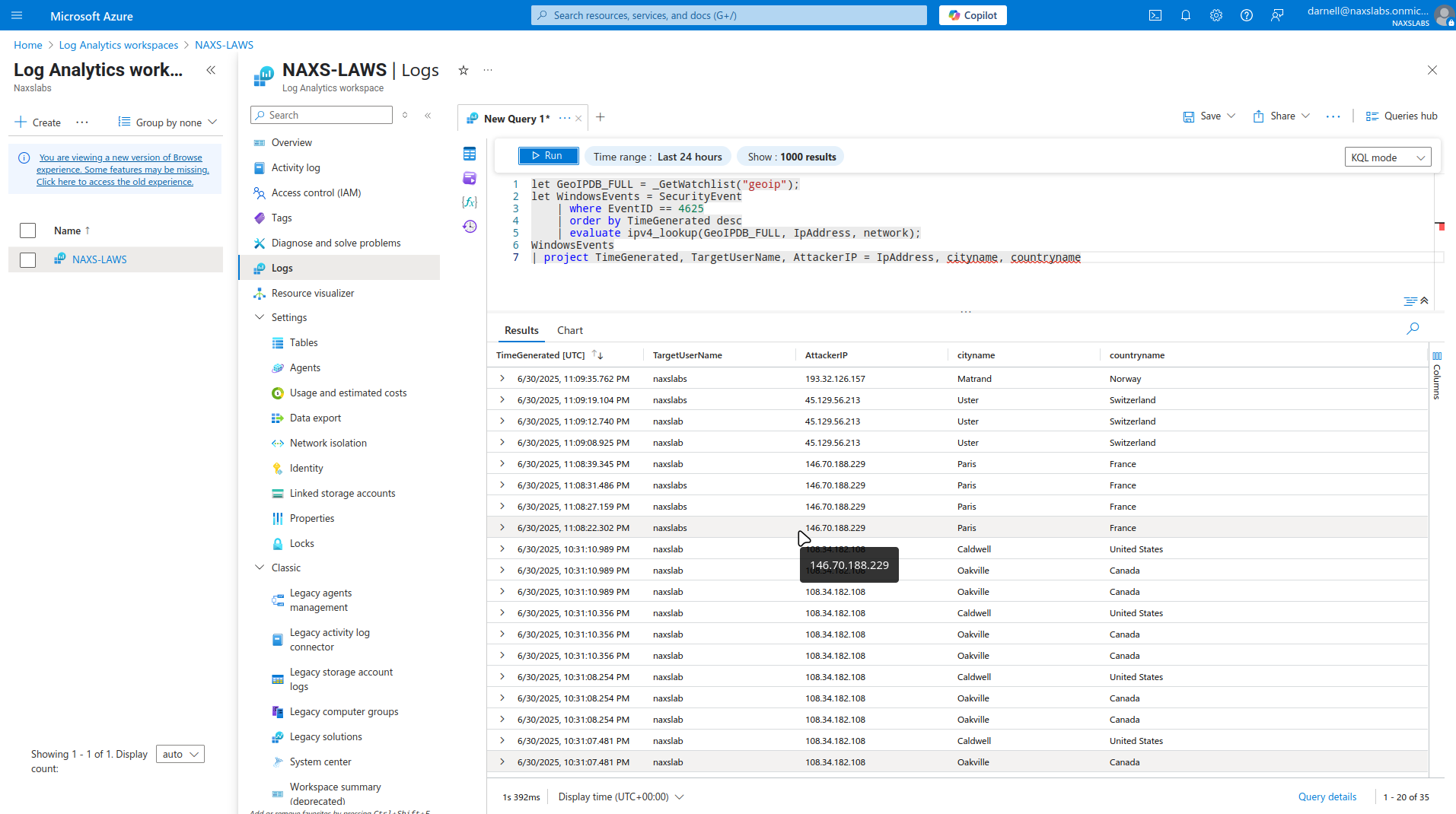
7. Geographic Data Integration
Create Watchlist for GeoIP Data
-
Prepare CSV file with geographic IP data containing:
- IP ranges or specific IPs
- Country codes
- Latitude/Longitude coordinates
- City/Region information
-
Upload Watchlist:
- Navigate to Sentinel > Configuration > Watchlists
- Click "Add new"
- Name:
geoip - Alias:
geoip - Upload the CSV file
- Set search key to network
Verify Watchlist Data
- Wait for upload completion
- Test watchlist query:
_GetWatchlist("geoip") - Verify data is accessible in KQL queries
8. Attack Visualization Workbook
Create Custom Workbook
- Navigate to Sentinel > Threat Management > Workbooks
- Click "Add workbook"
- Remove default template items
- Add new query visualization
[Screenshot: Workbook creation]
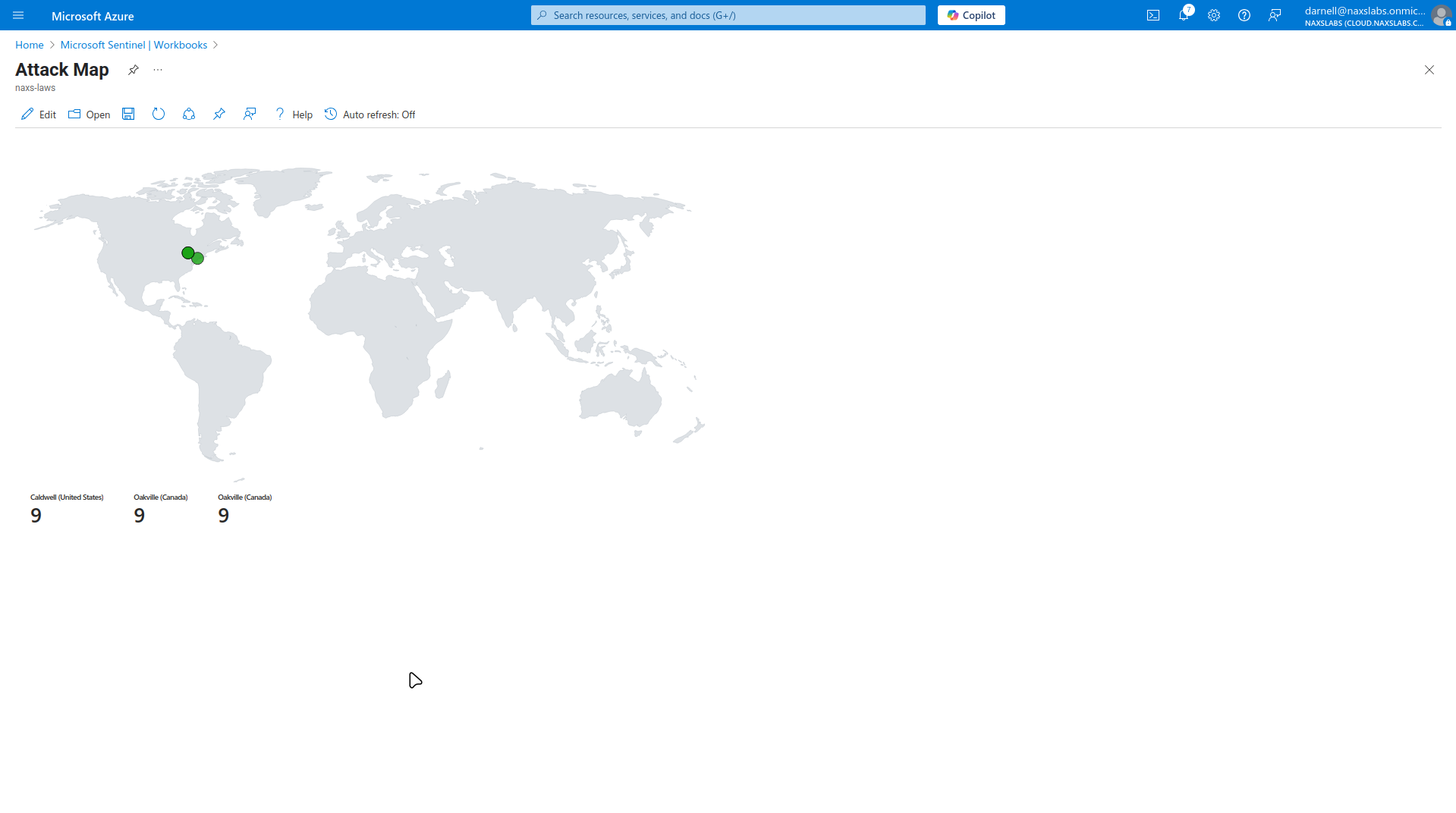
Configure Map Visualization
- Add Query Component:
- Click "Add" > "Add query"
- Select "Advanced Editor"
- Paste custom KQL query (See JSON file)
#### Save and Configure Workbook
1. Save workbook to appropriate region
2. Set auto-refresh intervals
3. Wait for login failures or simulate using a vpn
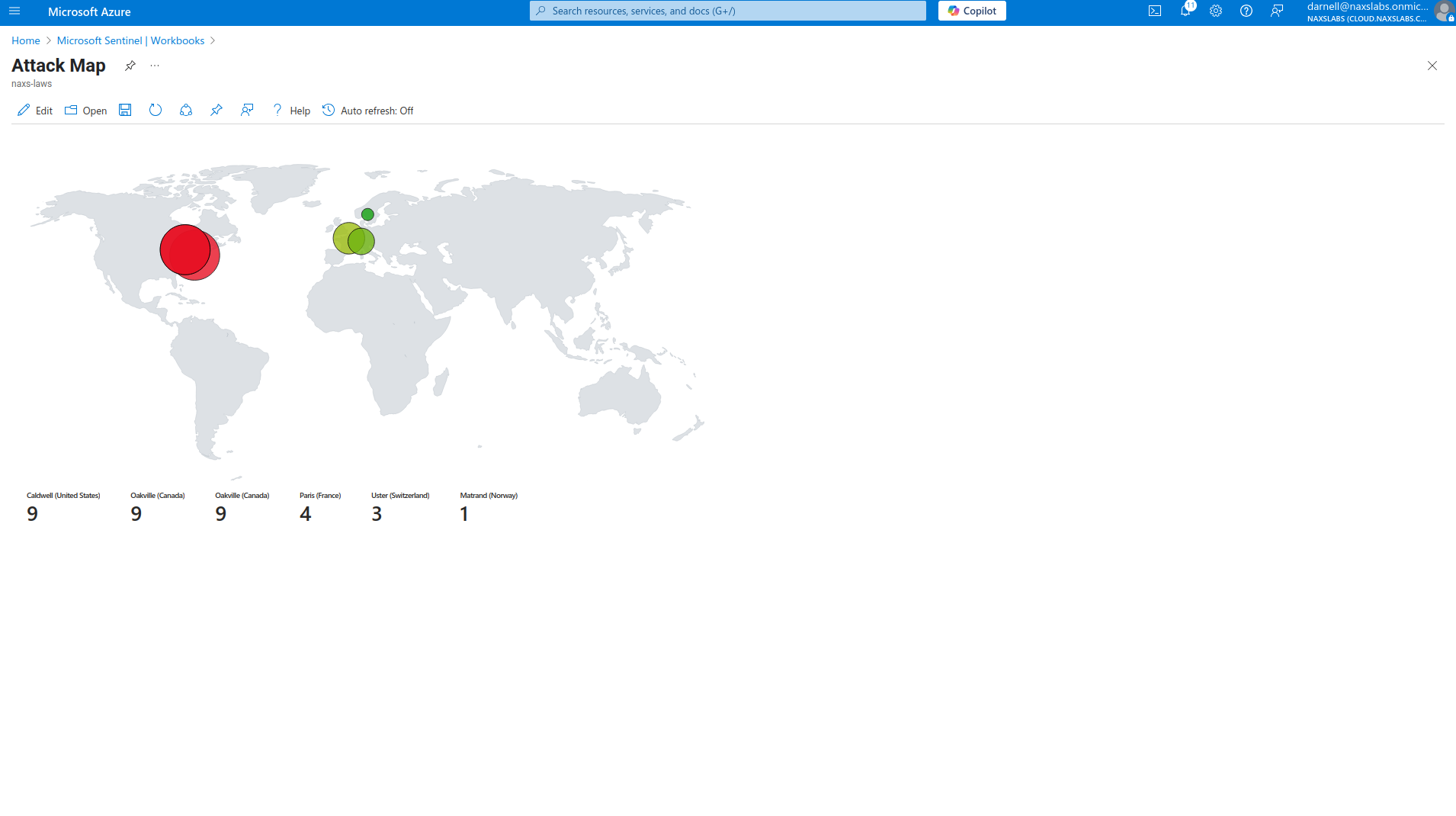
4. Test map functionality
Monitoring and Analysis
Key Metrics to Monitor
- Failed RDP login attempts (Event ID 4625)
- Source IP geographic distribution
- Attack frequency patterns
- Common username attempts
- Time-based attack trends
Sample Query
Security Considerations
⚠️ Warning: This project intentionally creates vulnerable infrastructure for educational purposes.
Important Notes
- Never use this setup in production environments
- Monitor costs as honeypots can generate significant traffic
- Regularly review and clean up resources
- Be aware of any potential legal implications in your jurisdiction
Cleanup Recommendations
- Delete resource group when project is complete
- Verify all associated resources are removed
- Check for any remaining charges
Troubleshooting
Common Issues
- No attack data appearing: Verify NSG rules are permissive enough
- Missing events: Confirm AMA agent is installed and data collection rules are active
Verification Steps
- Check VM is accessible via RDP from internet
- Verify Event ID 4625 events in Windows Event Viewer
- Confirm data flowing to Log Analytics Workspace
- Test watchlist queries in Sentinel
This project demonstrates:
- Real-world attack patterns and frequencies
- Geographic distribution of cyber threats
- Effectiveness of Azure Sentinel for threat monitoring
- Importance of proper security configurations
Next Steps
Potential Enhancements
- Add additional honeypot services (SSH, HTTP, etc.)
- Implement automated threat response
- Create custom analytics rules
- Integrate with threat intelligence feeds
Learning Outcomes
- Hands-on experience with Azure security services
- SIEM configuration and log analysis skills
- Network security and monitoring concepts
Disclaimer: This project is for educational and research purposes only. Always follow responsible disclosure practices and comply with applicable laws and regulations.